SCALYS
Secure by Design
Scalys products are Secure by Design. To ensure that devices are protected from the outset, cyber security must be addressed from the start of design. Through continuous innovation, collaboration and development, we ensure our position as leader in the market.

What is cybersecurity all about?
Cyber attackers are becoming more innovative, and there are more connected devices than humans. Cyber security is very important and is about protecting your networks, systems, and data to avoid losing IP or brand identity.
Why is it so important?
Protecting systems and networks from digital attacks is a necessity for every company or organization. A successful cyber attack results in accessing or changing data, destroying or taking data for ransom, possibly for extorting money, or loss of reputation. So, the negative side effect is that every attack disrupts the daily processes of companies resulting in even more loss of money.
Leader in cyber secure
communication
By understanding the market and knowing what challenges they face, Scalys helps its customers build the solution for their cyber security issues. Through continuously innovating and working with Industry-leading companies, we offer our customers future cyber security technology today.

Proven security
Delivering cyber security solutions is not just a claim. Our products are proven secure and certified. We are working together with test labs and certification bodies so we can ensure that our solutions will solve your security questions. We are familiar with IEC62443 all the way up to common criteria (ECN PP).
Collaborations
Scalys collaborates with Industry-leading companies in the fight against cybercrime. Together with our partners we strive for standardization, certification, innovation, to unburden companies with the difficulty of cyber security. And making the world a safer place. Join Scalys in the quest for better cyber security.
Ahead of the threat: continuous innovation
Our drive to create the ultimate cyber security solution pushes us to innovate continuously. Through collaborations with high-tech companies as customers, we create products that solve real-life problems. We realize innovations for your future needs through a strong foothold in every market.
Project CASSINI
Project Cassini is an open, collaborative, standards-based initiative to deliver a secure cloud-native software experience for devices based on Arm Cortex-A.
The approach of project Cassini is to have a set of base standards through platforms and security, and certification to check against these standards, validated with cloud native software, robust hardware and firmware and advocated through the Arm SystemReady program.
It has 3 pillars which are: standards, security, and cloud native stacks.
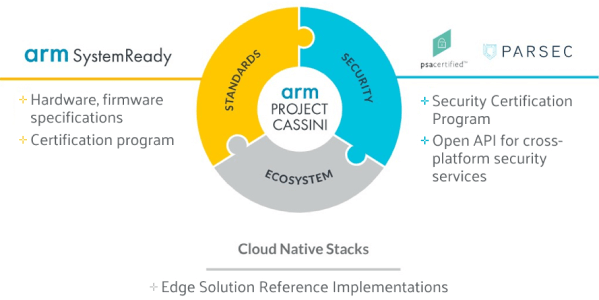
ARM System Ready
Arm’s SystemReady is part of the standards pillar and will ensure that generic “off the shelf” operating systems will simply work on Arm based systems.
As security standards nowadays used are very fragmented and diverse PSA certification will check against these standards. The PSA certification program is part of the security pillar which can be seen as a toolkit to use.
Parsec – open API for cross-platform security services
The approach of running applications on the edge rather than in the cloud emphasizes the reduce of latency and is providing more processing capability of data being closer to the source. But on the other hand, at the Edge, also increases the attack surface and this means a change in your threat model. An Edge device is more vulnerable, hence, IOT security plays a large and important role for Edge devices.
What makes it even more difficult is the diversity when it comes to hardware platforms. There are a diverse number of platforms with different operating systems and CPU architectures, different hard- and software-based root of trusts and a diversity in secure elements. This makes it rather complicated and sensitive to make
use of available security features, like a trusted platform module (TPM), hardware security module (HSM) or other secure elements, in the hardware. It is also time consuming to have these security features fully integrated and enabled on the platform you are developing.
Parsec is a part of one of the three pillars of project Cassini (read about Project Cassini here) and can be seen as software layer or interface between security features of the hardware and firmware to enhance the usability of these security features and to use them in a correct way. When using Parsec you can move a design to a different chipset without the need to change the language to make use of these features.
Simplified security framework
Parsec is a RUST based open-source initiative project. RUST is a great language for secure and reliable systems. Parsec runs as a service on an edge device communicating through a command line tool. Or even better, it can be integrated in the source code by talking to API’s for a simplified experience. Parsec translates these commands and takes care of a correct functionality of the security features on the device. Where other security primitives are designed to talk to one client only, Parsec is designed with multi-tenancy in mind. It is all about simplifying security when you incorporate Parsec in your security framework. This is exactly why Scalys embrace the use of Parsec within the TrustBox Edge family.
Using Parsec as a building block on our platform makes development goes faster with a quicker time to market, and even more important, it is improving security. In some use cases even customers of Scalys have the option to make use of security services on the platform using Parsec from within their application-level software.
Are you interested in learning more about Parsec? Information can be found at the following websites and/or Slack channel:
https://developer.arm.com/solutions/infrastructure/developer-resources/security/parsec, https://parsec.community/, https://dockercommunity.slack.com/
Confidential computing
Confidential computing augments traditional computing paradigms with additional protections for computing workloads and data when in use. Especially for IoT and cloud computing characterized by hyperconnectivity, multitenant compute infrastructures and data-driven autonomous command and control of many systems including critical infrastructure calling for a higher bar for privacy and safety.





